Operational Technology (OT) networks occur in numerous sectors, such as manufacturing, energy, transportation, and healthcare. Unlike traditional IT networks, disruptions or defects in OT networks can lead to production process downtime or safety system failures. Due to their critical nature, OT systems require a specific monitoring approach. The equipment must be able to process communications in real time and must never compromise the security or continuity of the network.
OT networks typically consist of legacy systems using proprietary industrial network protocols. These are not easily monitored with traditional IT tools. Gaining insight into these networks requires specialized equipment that can store the relevant information and interpret the protocols.
The Purdue Model
The Purdue Model for Securing Industrial Control Systems (ICS) is a framework that provides a layered approach to protecting sensitive industrial environments. The model was originally developed at Purdue University and further refined by the International Society of Automation (ISA) as part of the ISA-99 standard.
The model identifies six network segmentation layers, each with a specific function in managing and securing industrial operations — from the corporate network to the physical processes themselves.
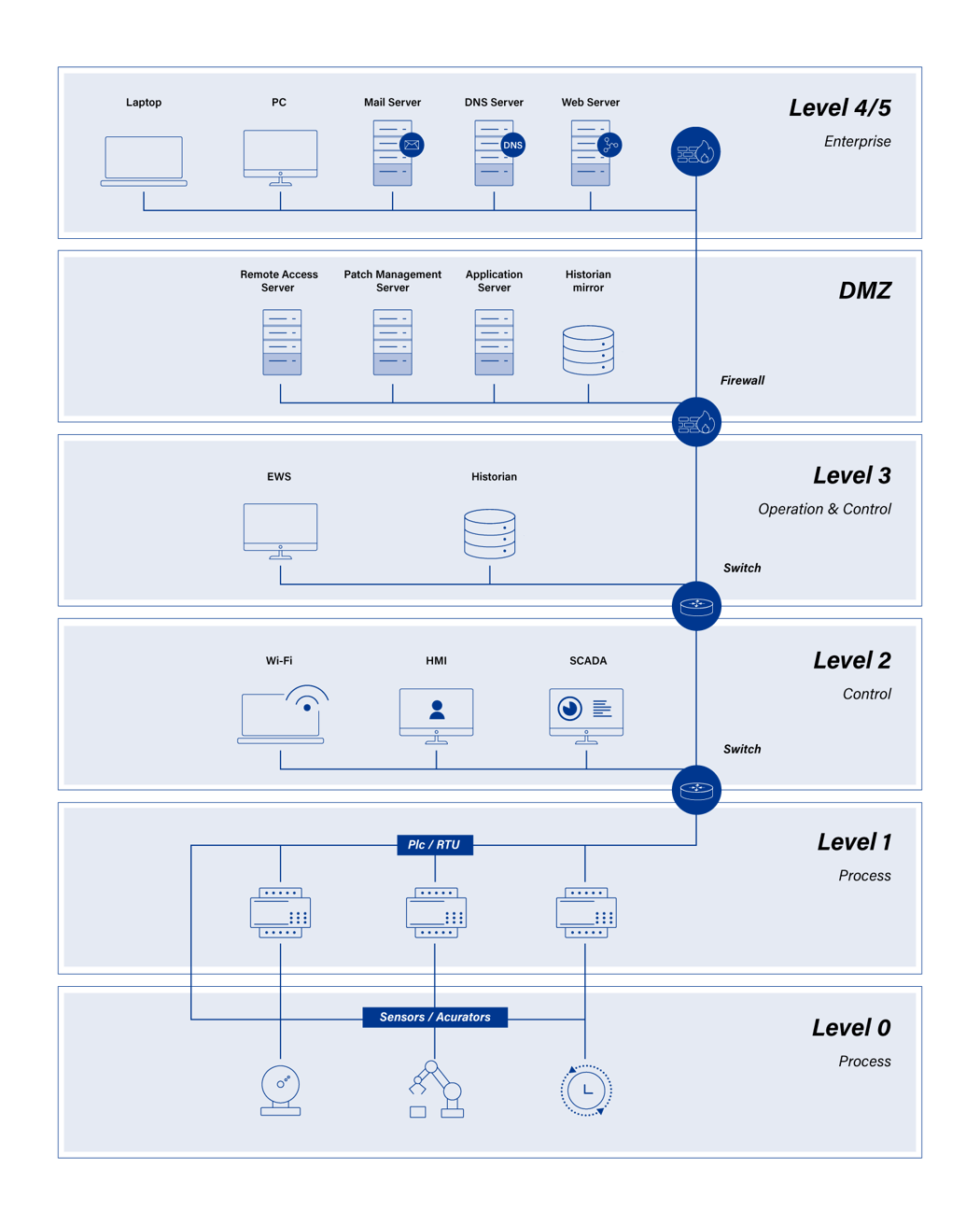
The main goal of the Purdue Model is to create clear, secure boundaries between the different layers of an organization, especially between the enterprise and production networks. This segmentation prevents the spread of cyber threats and strengthens the overall security structure. This structured approach allows companies to better manage risks such as cyber attacks, unauthorized access and data leaks, thus ensuring the reliable operation of these industrial control systems.
Monitoring OT networks according to the Purdue model
Step 1: Identify critical components
Identify the most critical components requiring protection — these are all the equipment and systems essential to running the process.
Step 2: Segment the network
Next, segment the network based on the hierarchical layers of the Purdue model. This simplifies monitoring and analysis, and shortens the potential recovery time in the event of an incident.
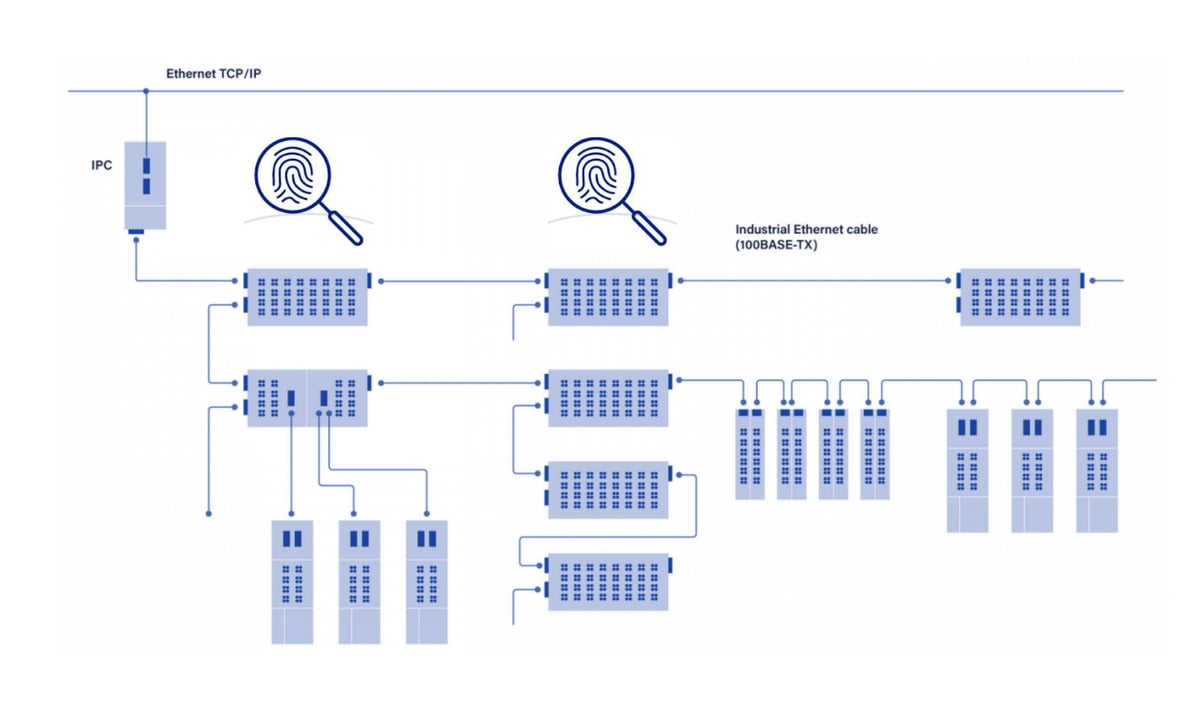
Step 3: Implement TAPs
Network TAPs are devices that can read all network traffic without disrupting it. Place them strategically, between different layers or zones, to read all communication.
Copper TAPs are non-intrusive devices that capture all network traffic on a single cable and deliver separate TX/RX flows without latency or interruptions. This allows them to be seamlessly integrated into existing networks—critical in industrial environments where timing is critical and disruptions can have significant impact.
.png?width=1200&height=654&name=enhancing-ot-network-monitoring-2%20(1).png?width=1200&height=713&name=Operation%20technology%20network%20diagram.jpeg?width=1050&height=1313&name=Purdue-graph-3.png)
Step 4: Aggregate and filter data
Use Booster Inline and Booster SPAN TAPs to consolidate network traffic from multiple TAPs into a single data stream. These devices are specifically designed to securely bundle and forward data to monitoring tools without loss. Their robust design and low latency make them ideal for industrial networks where reliability is paramount.
Step 5: Monitor network traffic
Using IOTA, all collected network communications can be stored on internal SSD storage and analyzed with various integrated dashboards. The data can then be forwarded to systems such as an Intrusion Detection System (IDS) or Network Detection & Response (NDR).
Step 6: Recognize deviations
Analysis tools can detect problems such as hacking, hardware degradation, bottlenecks, or defective components. Application administrators can take targeted action and select the best possible solution.
Step 7: Optimize and implement
Based on the insights gained, adjustments can be made to increase the resilience of the network and applications. Also at TAP and NPB level, additional capture points can be added or new filters can be set to get a better overview.
Step 8: Regular updates
It's essential to regularly update your monitoring and security tools to ensure they're equipped with the latest threat intelligence and functionality. This helps detect new attacks or technical issues early.
By following these steps, organizations can effectively monitor their industrial networks with TAPs and Booster aggregation TAPs, in line with Purdue's security model. This helps protect critical infrastructure from cyber threats, ensure operational continuity, and meet compliance requirements.